Detect stealthy attacks and insider activity that bypass other security controls.
Host-Based File Integrity Monitoring (FIM)
Host-based file integrity monitoring is often the only way to validate whether a threat has caused any genuine harm. Our file integrity monitoring (FIM) experts use proprietary technologies and processes to ensure the integrity of critical system files and detect unauthorized changes in real-time.
Service Overview
The Last Line of Defense Against Threats That Evade Your Firewall
Undetected cyber threats often remain undetected on target networks for weeks or even months. Our host-based intrusion detection system is your last line of defense against threats that evade your firewall, NIDS, and antivirus.
File integrity monitoring (FIM) tracks file modifications on a host, regardless of whether these changes were made by a user or a service. Quite often, this is the only way to validate whether or not an attack has been successful. In addition to being an essential component of any security program, FIM is also a core requirement of many industry compliance frameworks.
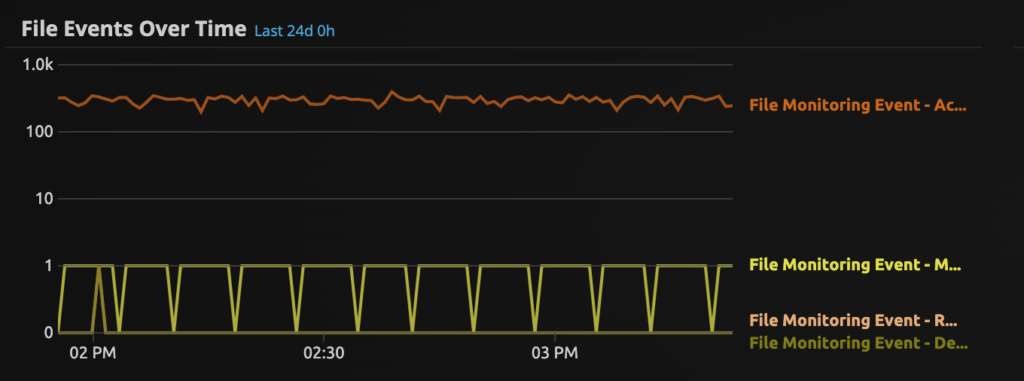
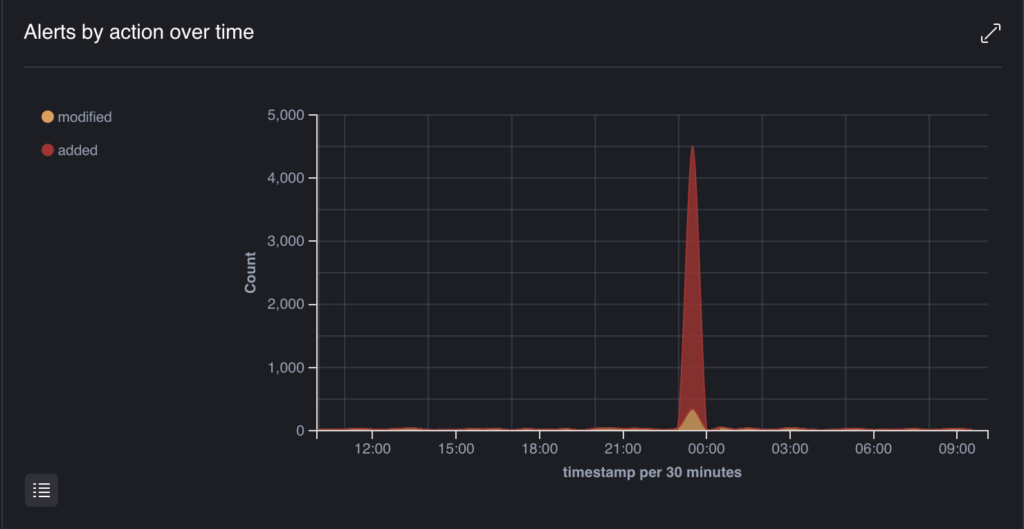
File Access Activity
Monitor for file access activity over time, the graphics show a spike in file access activity at a specific point in time. Spikes in file creation or modification can highlight suspicious activity, especially outside of business hours.
Unleash The True Power Of Your Managed Security Solutions
Our 24/7 Security Operations Center provides always-on threat hunting and investigation capabilities, and a member of our team is always available to answer your questions and address any security concerns. Best of all, you gain complete visibility into your threat landscape—allowing you to identify active threats in real time.
Key Benefits
Why File Integrity Monitoring Matters
Ensure the integrity of critical system files and detect unauthorized changes in real-time. Your last line of defense against threats that evade firewalls, NIDs, and antivirus solutions.
Protect critical files from unauthorized changes
Monitor and alert on any unexpected modifications to safeguard sensitive data and system integrity.
Suitable for all compliance frameworks
Meet requirements for PCI DSS, HIPAA, GDPR, and other regulations with continuous file integrity monitoring.
Last line of defense against sophisticated threats

Make Our Team, Your Team!
Our innovative IT security and compliance solutions are designed to deliver customized, cost-effective service on time—because your priorities are our priorities. With a highly qualified team of PCI DSS QSAs, Penetration Testers, and Information Security Consultants here at MegaplanIT, we will assess your unique company and business environment and design a path to security that will fit all of your needs.





























