
MegaplanIT
Security & Compliance
PCI DSS v4.0 Summary Of Changes
The long wait is over. Since the inception of version 3.0 of PCI DSS in February of 2014, we now have a new major release of the Payment Card Industry Data Security Standard in PCI DSS 4.0. The Payment Card Industry Data Security Standard, as it has evolved through minor releases, is enhancing the controls, testing, and applicability to a volatile landscape of payment card merchants and service providers. The changes to the standard, as with all releases, are designed to provide additional guidance and applicability to cardholder data environments and give those who leverage the standard additional flexibility when implementing security controls. The new standard will promote security as a continuous process, clarify objectives, and outline new testing requirements from previous versions.
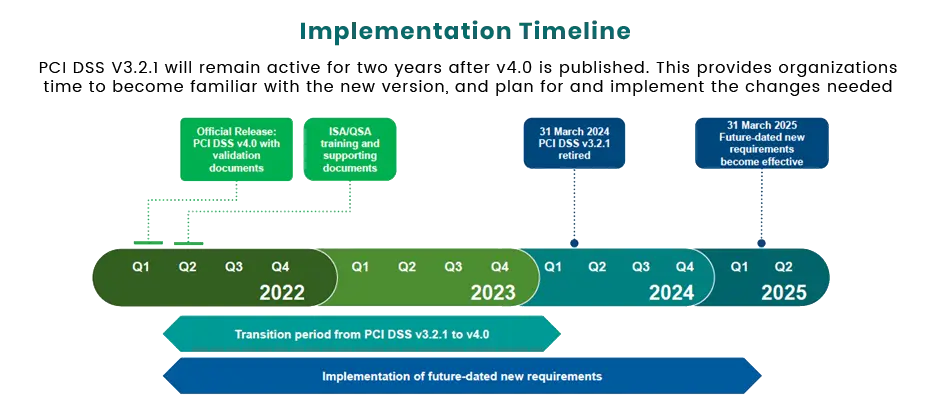
When can I expect to adopt the standard?
The predicted adoption of the standard is available on the PCI DSS council website and will feature a transition period for all parties to adopt the new standard. Much like the transition to v3.2.1 of the DSS, there will be a grace period to where future dated requirements will become mandatory (as with the retirement of TLS 1.0) followed by a retirement date for PCI DSS v3.2.1 where all merchants and service providers must adhere to the new standard. PCI DSS v3.2.1 will continue to be active until March 31st, 2024.
Outcome Based Testing/Customized Controls:
The landscape of the payment card industry continues to evolve as new products, technology, and processes pave the way for innovation. The council seized this opportunity to allow for controls to become outcome based and customizable as to be applicable to a broad spectrum of security implementation. Outcome-Based Testing and Customized Controls allow requirements not to be as constricting character length or password rotation but that “strong authentication for users and administrators is established and managed.” This may entail any of the authentication methods including passwords (something you know) or smartcards (something you have) or something you are (biometrics). The inclusion of these factors for a single factor of authentication expands on the DSS v3.2.1 as it simply included password credentials as a primary method of authentication. This expansion of requirement criteria is applicable to firewalls, cryptographic storage, or physical security.
Security Testing Above and Beyond
Security testing for PCI DSS 4.0 is getting reconditioned, in that security testing throughout the year will be required to more strict requirements compared to that of PCI DSS 3.2.1. Citing the PCI DSS 3.2.1 standard, there were fewer security controls to monitor systems throughout the year, such as quarterly internal (Requirement 11.2.1) and external vulnerability scans, (Requirement 11.2.2) as well as process examinations for service providers to ensure appropriate procedures were in place and being followed by the system administrators (Requirement 12.11).
New security testing standards will include an evolving requirement for 11.2.1, wherein other applicable vulnerabilities found during an internal scan must be addressed and managed. Internal scanning will also now require credentials for the scanning engine not previously required. Scanning engines with more permissions may produce more results as credentialed scans will have more insight into production systems. New penetration testing requirements for multi-tenant service providers is required for service providers. PCI DSS 4.0 implements a review of cryptographic suites used for transmission of cardholder data (Requirement 12.3.3) not found in the old standard.
Enhanced Multi-Factor Authentication Criteria
Multifactor authentication for administrative access into the cardholder data environment was adopted in v3.2.1 and has been a PCI standard since (Requirement 8.3). However, the implementation of multi-factor authentication for all users is a future-dated requirement in the PCI DSS 4.0 (Requirement 8.4.2). The new standard mandates that all access into the CDE be demarked by multi-factor authentication, causing both users and administrators to perform MFA at their workstations. Note, that as with the old Requirement 8.3, this does not apply for application or system accounts performing automated functions nor for individuals on POS systems who have access to only one credit card number at a time. There is also additional clarification on multi-factor authentication, where if the CDE resides within a corporate network, the demarcation point would be the boundary of the CDE, whereas if the CDE is entirely isolated and remote accessed, MFA would be required upon entering the CDE at that remote connection point.
Additional Firewall and Network Security Guidance
Requirements for firewalls are being updated as well, in that a wider range of network control devices are being considered and denoted. The PCI DSS 3.2.1 references with firewalls and routers have been replaced with a broader range of technologies to the evolving network control device technologies to be implemented. Additional guidance on appropriate inbound and outbound traffic for CDE networks was revised to make requirements easily applicable to different network topographies and ensure change control is appropriately documented and approved.
Storage of Cardholder Data and Encryption
Encryption and storage of cardholder data for PCI DSS 4.0 are more robust, in that many of the requirements have been enhanced or added in an effort to catalog cryptographic systems and processes as well as assign responsibilities for these elements. Sensitive Authentication Data (SAD) will now have storage requirements for pre-authorization (Requirement 3.2.1, 3.2.2) if stored within a CDE, whereas standard 3.2.1 did not address this issue. The new standard also outlines additional guidance on the appropriate deployment of disk or partition-level encryption standards for the protection of stored PAN within the production environment and removable stored media (Requirement 3.5.1.2).
Summary of Changes
There will be many changes to the PCI DSS 3.2.1ng technologies, network topographies, and third-party service provider relations. The new PCI DSS 4.0 standard boasts new requirements to address these areas and evolving requirements which would take the outlined standards one step further toward a more secure infrastructure. For additional information on these changes, review the summary of changes document available on the PCI-DSS council website.
Looking for a knowledgeable partner for your cybersecurity and compliance efforts?
The MegaplanIT team specializes in assisting businesses all around the world to achieve and maintain compliance. Our skilled security consultants and QSAs are fully certified to undertake PCI DSS v4.0 Assessments for your firm and have decades of expertise in assisting organizations like yours in staying secure and compliant. The level of support we offer is unmatched, and the knowledge of our team will help you overcome your goals. Set up a time to talk with us about your top payment security and compliance concerns so we can work together to solve them!
Share this post
Subscribe To Our Newsletter
Most Popular
Post By Topic
Compliance Services
Industry Leading Certified Experts




Subscribe
Subscribe To Our Newsletter & Stay Up-To-Date
Explore Our Blogs
Whitepaper | 10 min Read

Developing An Effective Compliance Program
This whitepaper provides organizations with a path forward. We will walk through aspects of an effective compliance program and how it can be valuable to your business. We will also outline critical steps towards developing and implementing a useful and effective Compliance Program.
New Service Offering | Contact Us

Ransomware Preparedness Assessment
As new vulnerabilities emerge in response to ongoing geopolitical threats, are you confident that your organization could defend against a ransomware attack? If not or if you are unsure, MegaplanIT is offering a Ransomware Readiness Assessment free of charge for up to 50 Systems.
ResourceGuide | 8 min Read

Cybersecurity Roadmap For 2022
Companies need to be aware of their current state, where they need improvement, and how to be proactive moving forward. Dialing in on the key elements your organization will need to succeed is a great starting point to having a full-fledged plan in place, and it all comes down to the fundamentals.
We're Here To Help
We look forward to talking to you about your upcoming Security Testing, Compliance Assessments, and Managed Security Services priorities. We are ready to help and discuss more information with you on our comprehensive list of services.

Make Our Team, Your Team!
Our innovative IT security and compliance solutions are designed to deliver customized, cost-effective service on time—because your priorities are our priorities. With a highly qualified team of PCI-DSS QSAs, Penetration Testers, and Information Security Consultants here at MegaplanIT, we will assess your unique company and business environment and design a path to security that will fit all of your needs.

Ransomware Assessment Preparedness

Cybersecurity Roadmap For 2022

Developing And Maintaining An Effective Compliance Program
As new vulnerabilities emerge in response to ongoing geopolitical threats, are you confident that your organization could defend against a ransomware attack?
A Cybersecurity Roadmap details priorities and objectives to drive progress towards security goals. The roadmap follows a data-driven path based on answers to critical questions
This whitepaper provides organizations with a path forward. We will walk through aspects of an effective compliance program and how it can be valuable to your business












